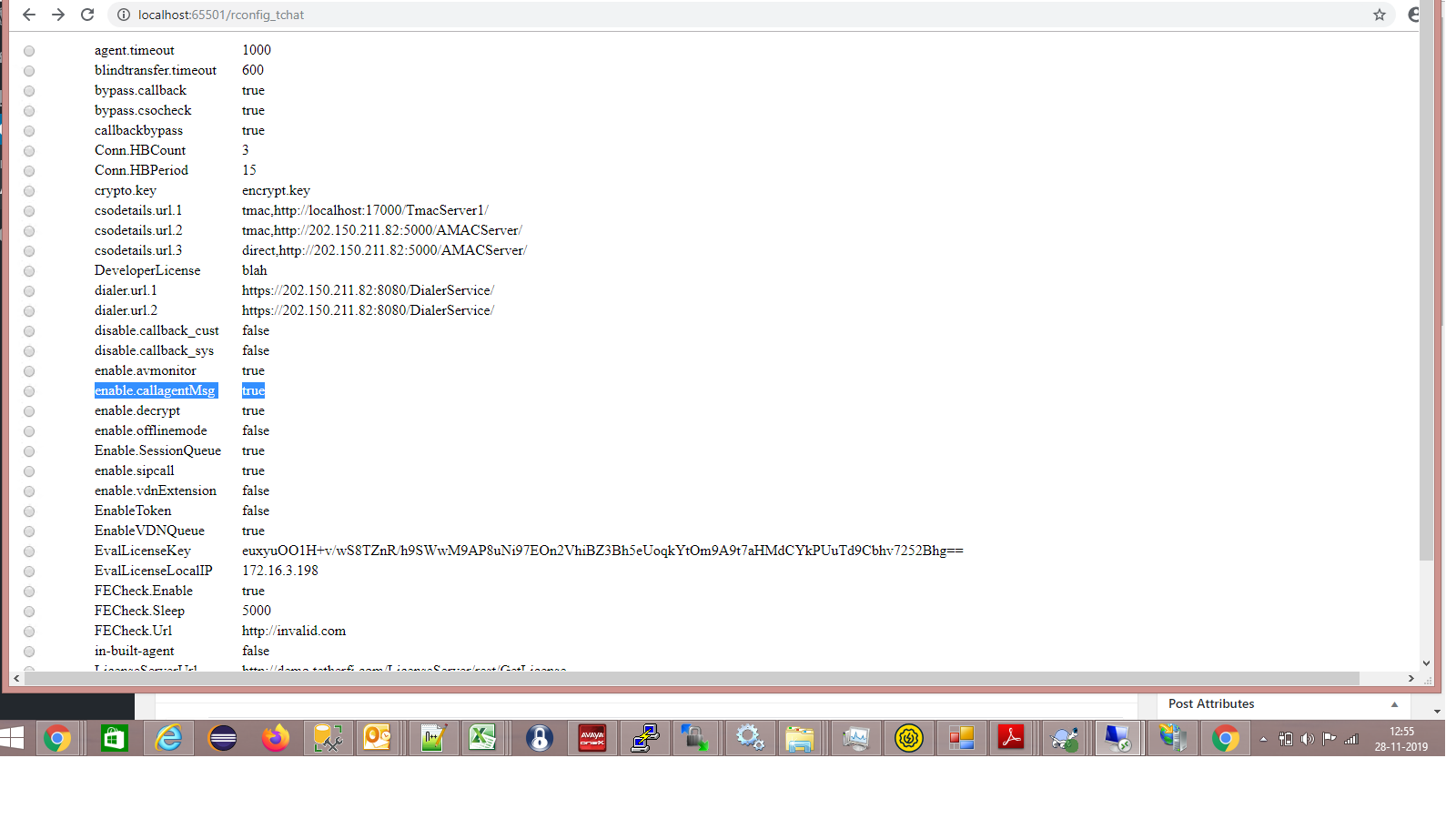
What is the issue?
An Improper Access Control vulnerability exists on the visual-ivr application. The /api/livechat/call/plaincall/__config endpoint allows unauthorized users to modify server configuration values such as UploadUrl and Proxy. This could lead to potential exploitation such as:
- Redirecting file uploads to malicious servers.
- Exfiltrating internal files through arbitrary path modifications.
- Exploiting Server-Side Request Forgery (SSRF) or unauthorized file reads.
How is this issue triggered?
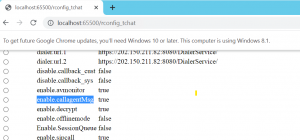
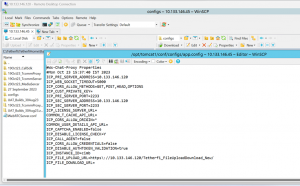
The issue occurs because the DWR (Direct Web Remoting) configuration object is exposed to client-side access.
Specifically:
- The /visual-ivr/ endpoint interacts with /api/livechat/.
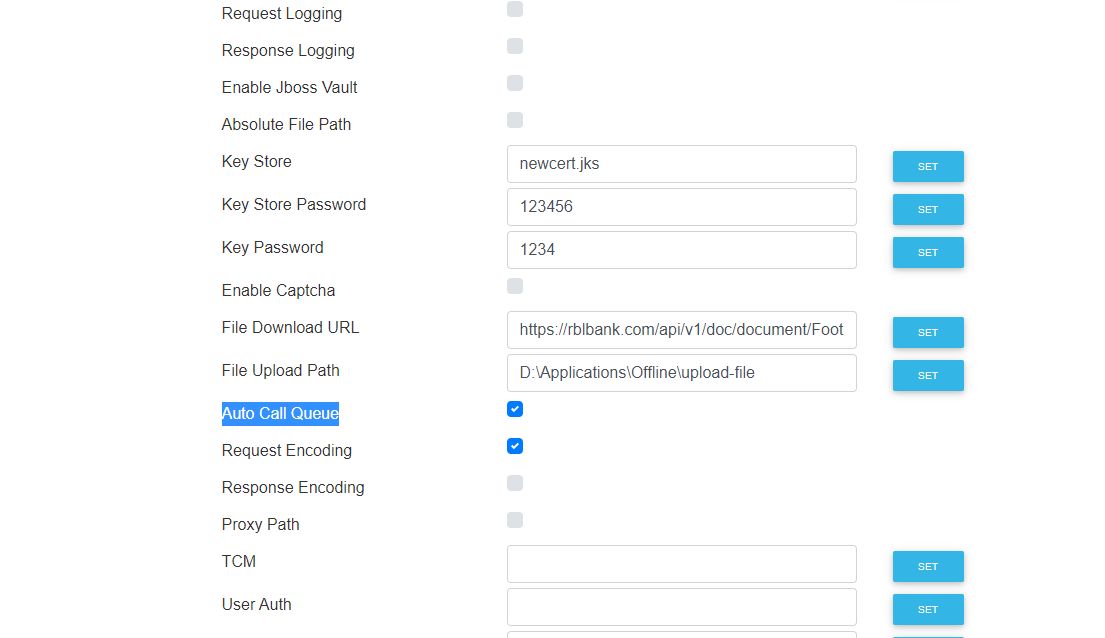
- The exposed methods setUploadPath and setDownloadURL allow attackers to change paths, enabling file exfiltration or downloading of internal files.
- Additional methods like setAllProxyURL and setServiceApiUrl could be exploited to manipulate proxy settings or API URLs.
Why is this a security risk?
The vulnerability introduces risks such as:
- File Upload Redirection: Attackers can modify the UploadUrl to redirect client file uploads to a malicious server.
- Internal File Exfiltration: The setDownloadURL method could allow reading internal files by pointing to arbitrary paths.
- SSRF and Misconfiguration: Exploiting other exposed methods can result in internal service compromise or sensitive data leakage.
How can the issue be resolved?
Remediation steps:
- Restrict DWR Configuration Access:
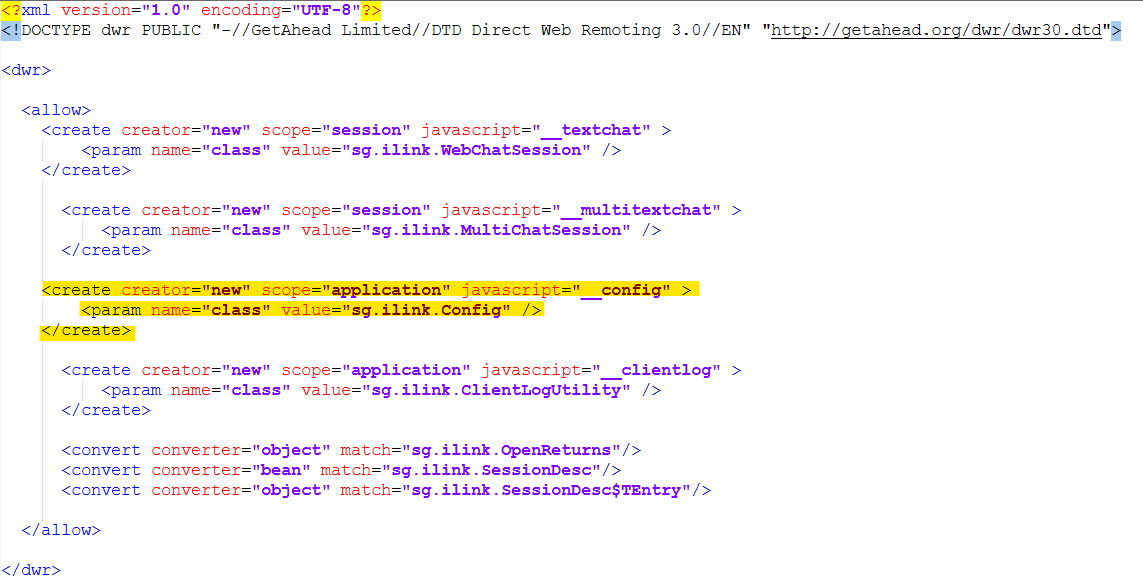
- Remove the __config object from being exposed by modifying the dwr.xml file in the application server.
- Action: Remove the following lines from <tomcat>/webapps/api/WEB-INF/dwr.xml:
<create creator="new" scope="application" javascript="__config"> <param name="class" value="sg.ilink.Config" /> </create>
- Remove Client-Side References:
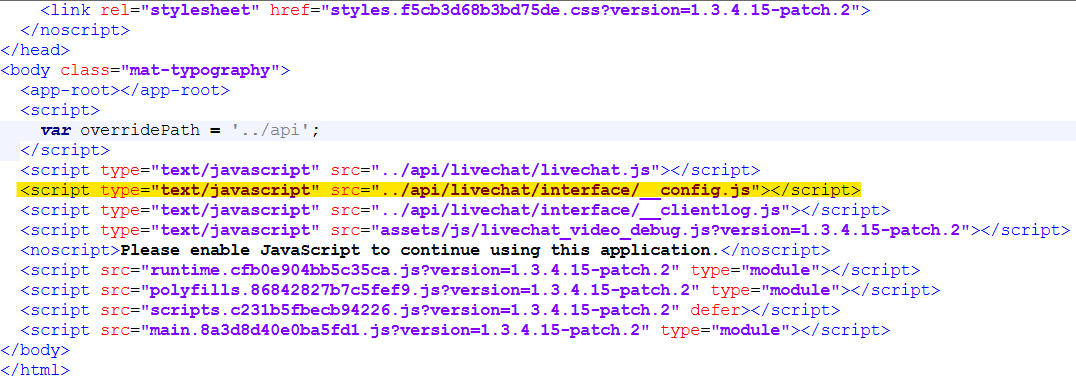
- Eliminate the script inclusion that exposes the __config JavaScript file.
- Action: Remove the following line from <tomcat>/webapps/visual-ivr/index.html:
<script type="text/javascript" src="../api/livechat/interface/__config.js"></script>
- Restrict Method Access:
- Implement proper server-side validation and access controls to prevent unauthorized usage of configuration-modifying methods.
- Validate all incoming requests at the API level.
- Deploy Secure Coding Practices:
- Ensure that sensitive configuration objects are not exposed through public endpoints or client-side scripts.
- Use role-based access control for administrative APIs.